I have completed the design and configuration of a highly-available, secure network in GNS3 for a project in my Masters studies. I chose to do this particular project because it would also help me to demonstrate my skills in network design and practical configuration skills. A preview of the network can be seen below:
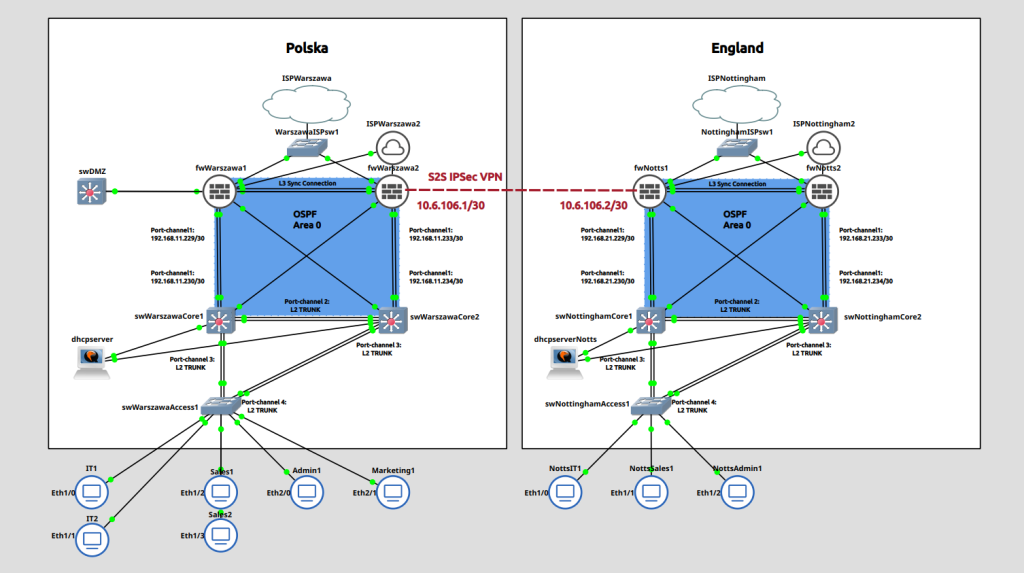
The network design features the following:
- Dual PFSense Community Edition firewalls at the edge.
- Site-to-Site IPsec VPN.
- Firewall rules on each interface to control traffic flow in the network.
- FRR OSPF package for redundant routing throughout the core.
- DMZ interface for public servers, such as a web server or authoritative DNS server.
- CARP Failover VIPs on the DMZ and WAN for automatic failover.
- Duel-WAN connection automatic failover.
- Dual Cisco L3 Core switches in the core.
- OSPF routing protocol (with MD5) for redundant routing throughout the core.
- VLANs to separate traffic for the following departments:
- 10 – IT
- 11 – SALES
- 12 – ADMIN
- 13 – MARKETING
- 14 – SERVERS
- VRRP VIP configured for each VLAN to provide redundancy in the core.
- DHCP relay to forward requests to the DHCP server.
- Debian server running ISC DHCP:
- Configured for each client VLAN.
- Bridge interface configured to talk to core switches.
- Link failure redundancy.
The below button will allow you to download the technical write-up for the project: